Multi-Factor authentication (MFA) is an extra layer of security, it is a combination of more then one credentials which authenticates the user example combination of user password with security token (software or hardware based), using of biomatric verification for authenticating the user credentials. By adding extra layer in security it make difficult for unauthorised person to get access of confidential resources like compute devices, network or database. It is helpful in case if one layer get compromised the attacker still has at least one more barrier to breach before breaking into the target successfully.
AWS also provides many MFA authentication mechanism: Virtual MFA devices, U2F security key, Hardware MFA device and SMS text message-based MFA. Read more for these MFA authentication mechanism
This tutorial cover how to install and use the Virtual MFA device app for authenticating your AWS login user id on AWS console.
Note: For installing Virtual MFA device app you need smartphone or tablet. The Virtual MFA device app should be AWS supported MFA device app such as Google Authenticator, Authy 2-Factor Authentication (for iphone and Andriod) or Authenticator (for Windows phone) which generates six digit code for authentication on AWS console.
I am using Google Authenticator on my Android based smartphone in this tutorial.
Installing of Google Authenticator on Andriod phone:
- Go to Google Play store search the Google Authenticator or aws mfa compatiable.
- Tap Google Authenticator> Tap install.
To Activate Virtual MFA device authentication:
- Login to AWS Management Console and access the IAM console at https://console.aws.amazon.com/iam/.
- In the navigation pane, choose Users.
- In the User Name list, choose the name of the intended MFA user.
- Choose the Security credentials tab. Next to Assigned MFA device, choose Manage.
- In the Manage MFA Device wizard, choose Virtual MFA device, and then choose Continue.
- From the wizard, choose Show QR code, and then from your smartphone use the installed Google Authenticator app to scan the QR code (In Google Authenticator this option available as scan a barcode) as Google Authenticator use camera for scanning QR code hence it will ask for permission to access camera first time so provide the same. Once you are done, the virtual MFA device app will starts generating one-time passwords.
- In the Manage MFA Device wizard, in the MFA code 1 box, type the one-time password that currently appears in the virtual MFA device. Wait up to 30 – 60 seconds for the device to generate a new one-time password. Then type the second one-time password into the MFA code 2 box. Choose Assign MFA.
Note: As code or OTP in Google Authenticator change in every minute you need to quickly put the code in request. You need to take backup of QR Code image or secret key in secure place so that in case of MFA Device App need to reinstall in your phone you can recover your MFA settings. If you lost the QR Code or Secret keys then you need to contact the AWS customer support team.
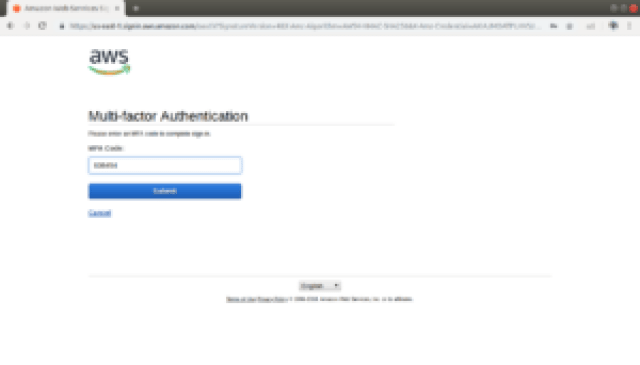
To testing the login authentication through Virtual MFA device app:
- Login to your AWS account link with Account ID, IAM user name and password
- In next page it will start asking you to put Multi-Factor authentication or MFA code generated on your Smartphone Google Authenticator App:
- Click on Submit. Voila, you have now access of AWS console from your user account.
Reference Sources:
https://searchsecurity.techtarget.com/definition/multifactor-authentication-MFA
https://docs.aws.amazon.com/IAM/latest/UserGuide/id_credentials_mfa_enable_virtual.html
![]()









This is Really Great blog, Which help me much more. I request to all you please refer this blog and grow your knowledge how to Multi Factor Authentication works.
Thanks Firoz